Web Application Development Cost: Complete Estimation Guide
Get a detailed breakdown of web application development cost. Learn the key factors, pricing models, and tips to estimate your project budget with confidence.
A Comprehensive Guide to Custom Web Application Development and Security
In today's digital landscape, web applications have become the backbone of modern business operations. From e-commerce platforms to enterprise management systems, custom web application development plays a crucial role in helping organizations streamline processes, enhance user experiences, and drive growth. However, as web applications become more sophisticated, they also become prime targets for cyber threats. Building secure, robust applications isn't just a technical requirement—it's a business imperative.
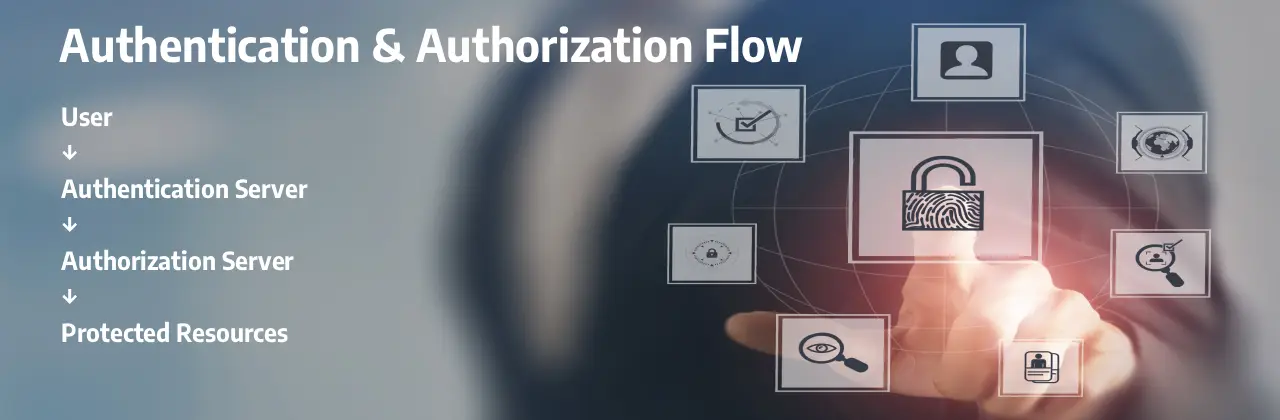
Multi-factor Auth
Token-based Sessions
Role-based Access
Encrypted Transfer
Custom web application development involves creating tailored software solutions that address specific business needs and challenges. Unlike off-the-shelf products, these applications are designed from the ground up to align with your unique workflows, user requirements, and strategic objectives. Whether you're building an internal tool for team collaboration or a customer-facing platform, the development process requires careful planning, skilled execution, and ongoing maintenance.
A professional web application development company brings expertise across multiple domains—from architecture and design to security and scalability. Their role extends beyond coding to encompass strategic planning, user experience optimization, and long-term support. When selecting web application development services, organizations should prioritize partners who understand both the technical and business aspects of application building.
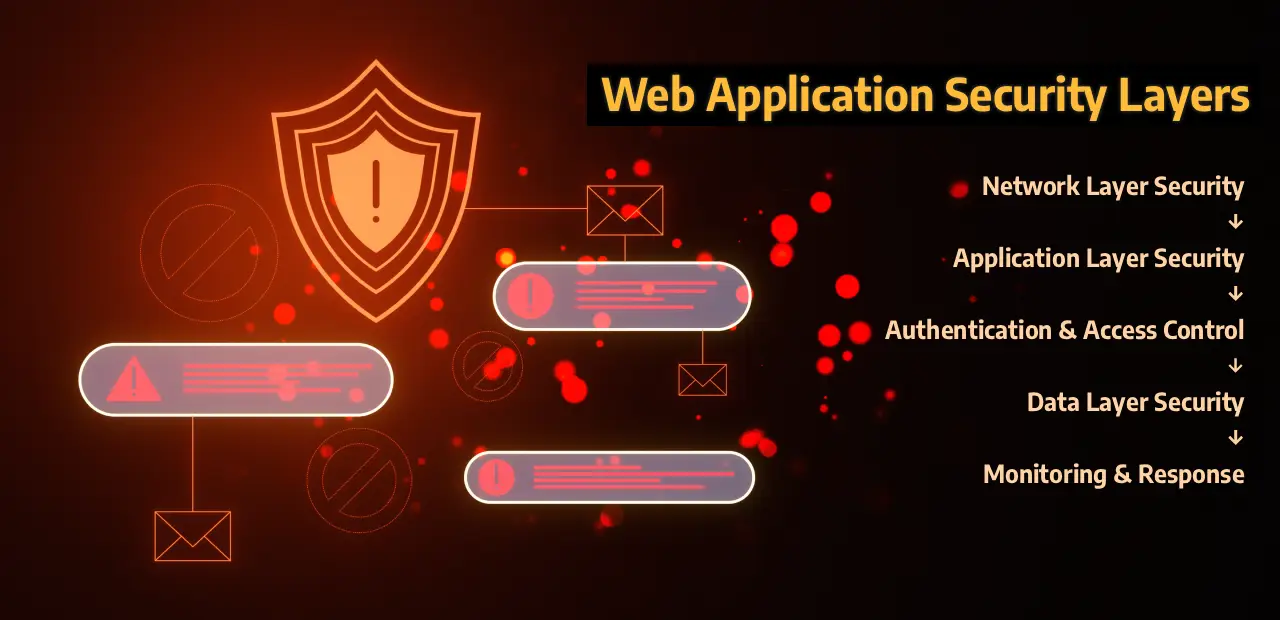
Comprehensive protection from external threats to internal data storage
Security must be embedded into every phase of the development lifecycle, not treated as an afterthought. Here are the fundamental principles that should guide your approach:
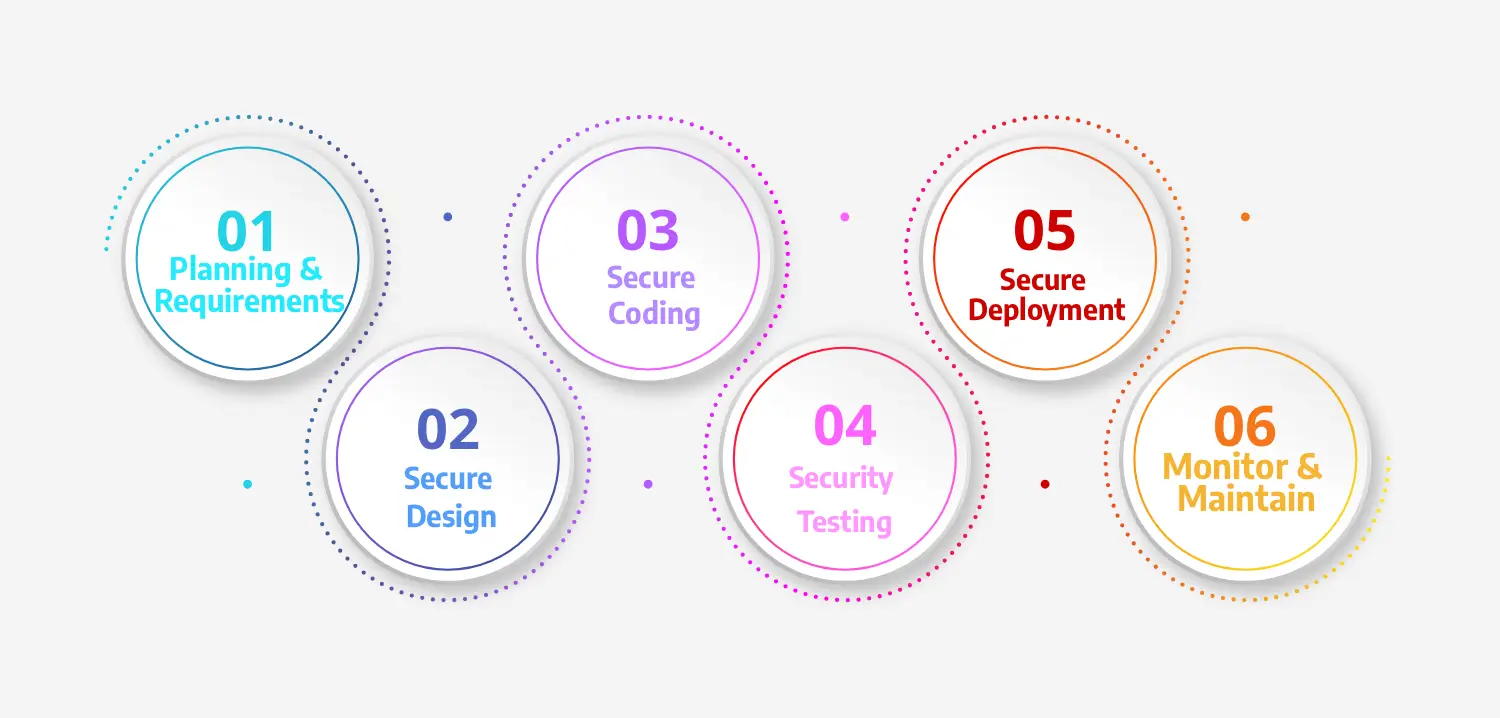
Continuous Security Integration throughout the entire development process
Successful custom web application development requires disciplined processes and collaborative teamwork. Here's how development teams can maintain quality and security standards:
The underlying architecture of your web application significantly impacts its security posture and long-term maintainability. Consider these architectural approaches:
Modern web application development embraces DevOps practices that integrate security into the continuous integration and deployment pipeline. This approach, often called DevSecOps, ensures security checks happen automatically throughout the development process.
Automated security testing should be part of your CI/CD pipeline, with builds failing when critical vulnerabilities are detected. Infrastructure as code practices help maintain consistent, secure configurations across environments. Container security scanning and runtime protection add additional layers of defense for containerized applications.
Depending on your industry and geographic location, web applications may need to comply with various regulations such as GDPR, HIPAA, PCI DSS, or SOC 2. Understanding these requirements early in the development process helps ensure compliance without costly retrofitting later.
A reputable web application development company will have experience navigating these compliance requirements and implementing necessary controls. This includes proper data handling procedures, audit logging, access controls, and documentation practices that meet regulatory standards.
Building a secure web application isn't a one-time effort—it requires ongoing vigilance and maintenance. Security threats evolve constantly, and applications must adapt to address new vulnerabilities and attack vectors.
Establish a regular patching schedule for all components of your application stack. Monitor security advisories related to your technology choices. Conduct periodic security assessments to identify new vulnerabilities that may have emerged as your application evolved or as new threats became known.
User awareness also plays a role in application security. Provide clear guidance on secure practices, implement strong password policies, and educate users about recognizing phishing attempts and other social engineering attacks.
When seeking web application development services, evaluate potential partners based on their security expertise and development methodologies. Ask about their security practices, testing procedures, and experience with relevant compliance requirements. A quality development partner will prioritize security discussions from the initial planning stages and demonstrate a track record of delivering secure solutions.
Look for teams that embrace modern development practices, maintain transparent communication, and show commitment to ongoing support and maintenance. The relationship with your development partner shouldn't end at launch—the best partnerships involve continuous collaboration to enhance, secure, and scale your application over time.
Building secure web applications requires a holistic approach that addresses technical, procedural, and organizational factors. Custom web application development offers the flexibility to implement robust security measures tailored to your specific risk profile and business requirements. By following these best practices—from secure coding standards to comprehensive testing and ongoing maintenance—organizations can create applications that protect sensitive data, maintain user trust, and support long-term business objectives.
Security isn't a feature to be added at the end of development; it's a fundamental aspect that must be woven into every decision from initial architecture through deployment and beyond. Whether you're building applications in-house or partnering with external experts, prioritizing security from day one will pay dividends in reliability, compliance, and peace of mind.
Get a detailed breakdown of web application development cost. Learn the key factors, pricing models, and tips to estimate your project budget with confidence.
Learn how to choose the best technology for web development. Compare tech stacks based on project needs, scalability, cost, team skills, and long-term goals.
Discover how AI improves modern web and mobile applications with automation, personalization, speed, and smarter user experiences. Learn the key benefits.
Get in touch with Prishusoft – your trusted partner for custom software development. Whether you need a powerful web application or a sleek mobile app, our expert team is here to turn your ideas into reality.
